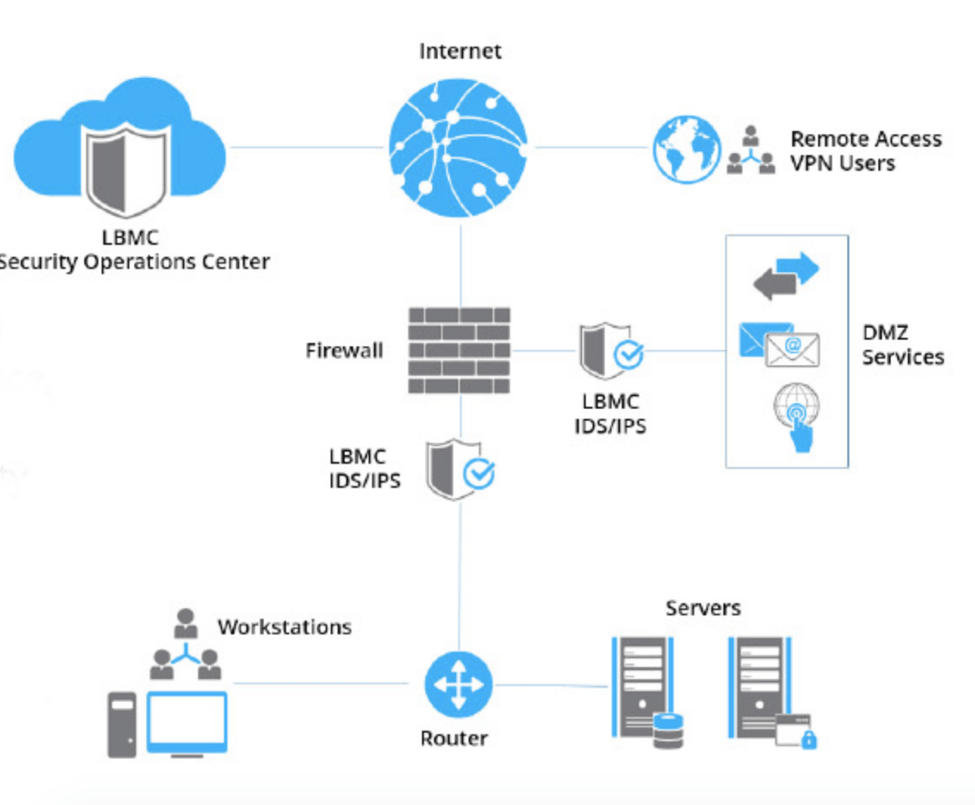
Losing sensitive information because of a cyber attack has been a concern for businesses and enterprises for nearly two decades. In the early 2000s, intrusion detection systems (IDS) and intrusion prevention systems (IPS) became a security best practice to help businesses protect themselves against evolving data breaches. Before then, firewalls had been very effective in countering the threat landscape of the 1990s.
IDS vs. IPS
While the systems have changed over time, having a robust IDS/IPS system in place is just as critical today. So what role to IDS/IPS systems play in today’s cybersecurity landscape? This article covers how each system works, how they are different and why you need them.