We’re going to look into some of the biggest trends impacting the IT security industry and highlight some important action steps your organization can take to stay ahead of the hackers. But before we look at the future of cybersecurity, we wanted to take a look back at some of the largest (and most expensive) data breaches of 2017.
4 of the Most Expensive Cyber Attacks of 2017 (and How They Could Have Been Prevented)
1. Equifax
Estimated Cost: Up to $4 Billion
The Equifax data breach quickly moved up the ranks as one of the worst cyber security attacks in history after the personal information (including Social Security Numbers, birth dates, addresses, and in some cases drivers’ license numbers) of 143 million consumers was exposed. While it will take a little while for the dust to settle, the initial impact is brutal. Equifax lost $4 billion in stock market value since the credit bureau revealed that it was hacked.
How It Could Have Been Prevented:
While Equifax appears to have a robust cybersecurity program in place, it is evident that accidents happen. The massive data breach could have possibly been avoided if Equifax had put additional security measures in place. Independent vulnerability validation process, a proactive approach to cybersecurity, and a layered, defense-in-depth strategy are just a few ways the Equifax breach could have been avoided.
2. WannaCry
Estimated Cost: Up to $4 Billion
Until Equifax, WannaCry held the title as the most unprecedented cyberattack of the year because of the incredibly broad impact that affected computers worldwide and how fast the attack spread. Once WannaCry was activated to unleash devastation, it quickly spread to reportedly more than 100 countries in less than 24 hours. And while the Ransomware attackers only received over $140,000 in bitcoin from the operation, a report by CBS News said that the losses due to the ransomware attack were estimated to reach around $4 billion!
How It Could Have Been Prevented:
What made the WannaCry ransomware particularly upsetting was the fact that ransomware attackers attached through a vulnerability that Microsoft had discovered and issued a security patch for a couple of months early. Hackers were counting on organizations being slow to apply the security patches. Protecting your company against malware attacks requires you to consistently and proactively protect yourself. Our team at LBMC has developed a comprehensive checklist to protect your organization from ransomware attacks that you can use to build defenses against most malware, not just WannaCry.
Why was WannaCry such a big deal? It spread. FAST!
Those of us in the cybersecurity field had not seen anything with this much potential for widespread devastation in over a decade. The authors of this malicious software (malware) took the already devastating impact of ransomware infecting a single computer to encrypt files to creating armies of computers within an organization to encrypt every user file they can modify. Cybersecurity experts had feared the potential of ransomware advancing to the next level for years.
The WannaCry infections likely started weeks before but remained dormant until the malware author felt enough devices were infiltrated before remotely activating the spreading and encryption features. Once WannaCry was activated to unleash devastation, it quickly spread to reportedly more than 100 countries in less than 24 hours. Notable impact included 16 hospitals in the NHS that had to cancel surgeries, a large telecom company in Spain, and FedEx. The Japan and China were hit and reports indicated more than 300,000 computers had been infected.
The WannaCry malware only targets certain versions of Microsoft Windows. Once the Windows computer is infected, it reportedly crashes with the “Blue Screen of Death” (BSOD) or simply reboots the computer and displays the ransom note requiring $300 worth of bitcoin, an untraceable Internet currency.
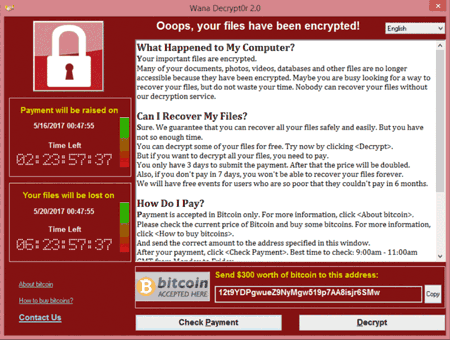
Why not pay the $300? The ransom was $300 per computer. If your organization has 200 computers infected with WannaCry, that is $60,000 for the needed decryption keys. Even if you paid the ransom, there was no guarantee that your files will be restored.
Fortunately for most, the WannaCry “Kill Switch” was actually discovered by accident which arguably reduced the damage of WannaCry significantly. However, WannaCry 2.0 has been released and has no kill switch. And you can be certain that ransomware authors worldwide took note of the potential WannaCry exposed and are working diligently to capitalize quickly. Therefore, businesses of all sizes must take the appropriate steps to protect themselves.
3. Petya/NotPetya
Estimated Cost: $300 Million (for both Maersk & FedEx)
Not long after WannaCry, another ransomware attack made headline news because of its global impact. While the Petya/NotPetya didn’t affect nearly as many organizations as WannaCry, the destructive force it had on the organizations that were affected was catastrophic. Most of the victims were in Russia and Ukraine. However, major companies in the West also suffered from the attack, including FedEx and shipping giant Maersk, both of which estimate $300M in lost earnings.
How It Could Have Been Prevented:
Similarly to WannaCry, Petya/NotPetya encrypted user’s data and asked for a ransom in exchange for restoring your documents. And like WannaCry, Maersk and FedEx could have avoided being affected by applying the Microsoft security updates and patching software.
4. Washington State University
Estimated Cost: $630,000+ fines
For the seventh year in a row, healthcare distinguished itself as the most expensive industry for data breaches. Washington State University was one of the latest victims after a hard drive containing the personal data of about 1 million people was stolen in April. While the HIPAA fines have not been issued by the Office of Civil Rights, the company has already experienced significant hard costs from the breach, including the deductible for their cybersecurity insurance and mailing costs to notify patients affected.
How It Could Have Been Prevented:
Unlike the other cyber attacks on our list, Washington State University’s attack happened because their physical hard drive was stolen. An important reminder that your cybersecurity program should include a plan for protecting your facilities and other places where patient data (including backup data) is stored. It’s also noteworthy that simply having proper encryption technology in place would have made this a non-story. Having the proper security systems in place is not only important for your patients’ physical safety, but also for the safety of sensitive data.
In working with clients of all sizes and all verticals to build resiliency against ransomware and other types of malware, LBMC developed a comprehensive checklist that can be downloaded. Many of the items listed are long-term remediation efforts. LBMC recommends that you take the following steps to protect yourself immediately:
- Ensure your backups are working properly
- Warn your users NOT to open attachments from unknown sources or from known sources that they are expecting attachments from
- Do NOT rely on Anti-Virus as the sole protection mechanism
- Patch all your Windows Systems Immediately to the latest level from Windows Update
- Patch third party applications such as Internet browsers, Adobe, Java, etc.
- Prevent the delivery of .exe files or .zip through your email system
- Disable “Active Content” (aka Macros) in Microsoft Office Documents
Malware isn’t new. Ransomware isn’t new. Take action now.
This epidemic of hacking does not show any signs of stopping anytime soon. The more interconnected our world becomes, the higher the risk of security breaches. But by having the proper risk management processes in place, companies can work to avoid the incredibly expensive costs of a data breach.
